When you are constantly in the realm of cutting edge technology, blog your message out might reminds you in the future how foolish those technologies can be.
(Also, One of the many silly KLSE blog, :P)
Hey Read This, this blog is purely representing the perspective of a nerdy geek and please don't take the contents too serious. For professional advices, please contact me personally :)
Friday, November 03, 2006
Information Security Consciousness in Malaysia
I recently ran a network scan on some of the local IP segments in Malaysia, the results are within my expectation, i.e. quite a number of broadband service subscribers in Malaysia doesn't realize about the risks of their computers being exploited in the Internet, or maybe they just not literate enough to have such awareness. I seen file servers that are exposed to the Internet and yet share out some folders that store critical information like daily transaction files, quotations, and even human resources payroll data files. What will happen if I'm one of those destructive people that just go in and wipe everything out? Voila, they better have a pretty good business continuation strategy. Also, one thing I noticed is that these machines usually infected by some dated viruses and trojan horses like NetBus and BO. O yes, I forgot to mention that gigabytes of porn materials and illegal software are found in these HDD.
Friday, October 27, 2006
Do you believe in God?
Well, I don't believe in God. I DO believe in Gods, indeed a fan of polytheism. I pray to lots of Gods day and night. And here is Their response.
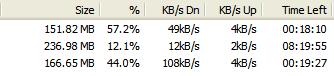
Finally, somehow I think the ADSL line is uncapped or losing it's control and my Bittorrent download speed reaching 185KB/s, which is so cool (Well, just don't compare to the 8Mb line in Japan or elsewhere)
And Gods, I praying to You still. Please grant me a 8Mb line and forgive this tiny little greedy mortal.

Finally, somehow I think the ADSL line is uncapped or losing it's control and my Bittorrent download speed reaching 185KB/s, which is so cool (Well, just don't compare to the 8Mb line in Japan or elsewhere)
And Gods, I praying to You still. Please grant me a 8Mb line and forgive this tiny little greedy mortal.
My Preciousssssss (Will it be Ruby?)
Ok, here's the question.
Which one of the following is programmer's best friend? (See hints)
a. Ruby
b. Java
Hints:
 Java's logo
Java's logo
 Ruby's logo
Ruby's logo
Answer:
Well, it's sort of depends on whether you as a programmer like to drink coffee, especially Java type, or you rather earn more money (by selling Ruby?) and eventually afford to drink more exotic coffee than Java. For me, I think it's no harm to do both things at the same time, and why not. :p
Which one of the following is programmer's best friend? (See hints)
a. Ruby
b. Java
Hints:
 Java's logo
Java's logo Ruby's logo
Ruby's logoAnswer:
Well, it's sort of depends on whether you as a programmer like to drink coffee, especially Java type, or you rather earn more money (by selling Ruby?) and eventually afford to drink more exotic coffee than Java. For me, I think it's no harm to do both things at the same time, and why not. :p
Thursday, October 26, 2006
Enable Commenting (Comments)
An excerpt from Alphablox 8.4 documentation:
Here is what you need to do to get a feel of the built-in CommentsBlox in Alphablox.
First, go to Alphablox Administration Site, by default should be accessible from http://yourserver:9080/AlphabloxAdmin/
From the Administration main tab, you should be in General paage by default. There is a Runtime Management section, amongst others. Click on the Comments link under this section. A pop-up window should appear that refer to http://yourserver:9080/AlphabloxAdmin/comments/commentsAdmin.jsp.
Here you gotta define the comments collection (sort of like a repository to store a particular set of comments) and maybe customize the set of fields used for commenting.
Choose a data source that you already defined elsewhere, enter the security credential and click Connect button. All existing collections should appear in the list provided.
Click Create button, since you want to create a new collection. You need to fill in the details for the form provided, particularly you need to specify the dimension to enable the comments and the fields required for the comment entry.
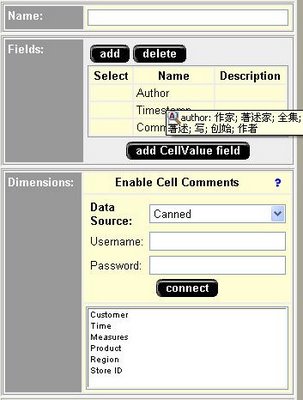
Click Save once you done.
Ok, you have done with the necessary configuration.
In your Blox programming, you can do the following:
1. Enabling Commenting for GridBlox
...
<blox:data><blox:comments collectionName="YourCommentCollectionName" dataSourceName="TheDataSourceUsedForCollection" /></blox:data>
...
...
<blox:grid commentsEnabled="true" />
...
Then when you right click on your grid cell, an option called "Comments" will appear.
2. Use com.alphablox.blox.CommentsBlox and related com.alphablox.blox.comments.*
This allows you to implement Commenting feature for your relational reports or any other general usage. Requires programming though.
CommentsBlox allows you to provide cell commenting (also known as cell annotations) functionality to your application. In addition, you can use CommentsBlox for general commenting that are not tied to any other Blox. For example, you can allow users to add comments to a site, an application, a report, or a Web page.
Comments are stored in a JDBC accessible relational database. Supported databases include IBM(R) DB2(R) UDB, Sybase, Microsoft(R) SQL Server, and Oracle. This data source needs to be defined to DB2 Alphablox. DB2 Alphablox provides a Comments Management page under the Server link in the DB2 Alphablox Administration tab that lets you specify the relational data source to use for storing comments. From that page, you can create "collections" (data tables) to store comments. For cell-level comments, you will need to specify the multidimensional data source used in your GridBlox, the cube to use (for Microsoft Analysis Services), and the dimensions to include. For general comments, you only need to specify the name.
Here is what you need to do to get a feel of the built-in CommentsBlox in Alphablox.
First, go to Alphablox Administration Site, by default should be accessible from http://yourserver:9080/AlphabloxAdmin/
From the Administration main tab, you should be in General paage by default. There is a Runtime Management section, amongst others. Click on the Comments link under this section. A pop-up window should appear that refer to http://yourserver:9080/AlphabloxAdmin/comments/commentsAdmin.jsp.
Here you gotta define the comments collection (sort of like a repository to store a particular set of comments) and maybe customize the set of fields used for commenting.
Choose a data source that you already defined elsewhere, enter the security credential and click Connect button. All existing collections should appear in the list provided.
Click Create button, since you want to create a new collection. You need to fill in the details for the form provided, particularly you need to specify the dimension to enable the comments and the fields required for the comment entry.

Click Save once you done.
Ok, you have done with the necessary configuration.
In your Blox programming, you can do the following:
1. Enabling Commenting for GridBlox
...
<blox:data><blox:comments collectionName="YourCommentCollectionName" dataSourceName="TheDataSourceUsedForCollection" /></blox:data>
...
...
<blox:grid commentsEnabled="true" />
...
Then when you right click on your grid cell, an option called "Comments" will appear.
2. Use com.alphablox.blox.CommentsBlox and related com.alphablox.blox.comments.*
This allows you to implement Commenting feature for your relational reports or any other general usage. Requires programming though.
Labels:
Alphablox,
Data warehousing,
DB2,
Java,
Programming Tips,
Tips and Tricks
How to enable your UBUNTU to play RMVB media files
For UBUNTU distribution of Debian/Linux, it is often easier to obtain and install the software applications you need from reliable sources.
The GUI Based of package management tool (Synaptic Packager Manager) alleviates the prerequisite of understanding and using apt-get, wajig and other similar kind of utilities.
Here, I presented a step by step guide on how to setup your UBUNTU box to enable it to play RMVB (A famous media file format, usually used to share video on BitTorrent network in Asia).
Step 1:
From the taskbar, access Application then Add/Remove Applications.
Once activated, the program need to conduct some checks on installed components and their dependencies and etc. You just gotta wait.
Step 2:
Click on the Advanced button on your bottom left corner of the Add/Remove Applications window.
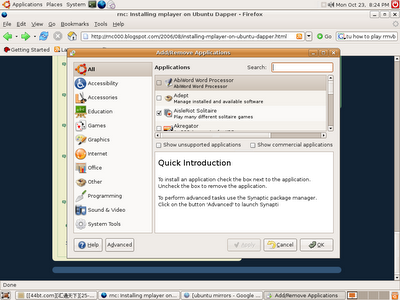
Step 3:
Then you will be in Advanced mode.
Note: The system might prompt you to enter password for authorization.
Step 4:
You need to add a new entry to the repository. Activate the repository settings screen through Settings -> Repositories from the same window.
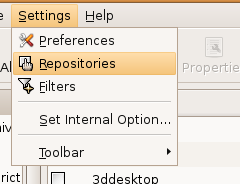
Step 5:
Add a new channel, by click on Add button.
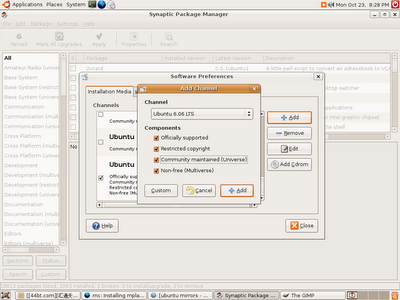
Make sure you select all the options on the Add Channel screen. and click Add.
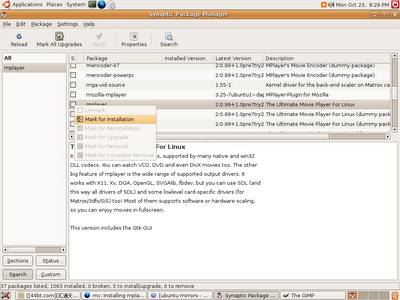
Step 6:
Once added, you click on the Reload button on your top left corner to refresh the list of programs. Then You can start to search for this software called "mplayer".
Click on the Search button on the menu bar, and enter "mplayer" and hit search.
The search results should be displayed on the pane at your right handside.
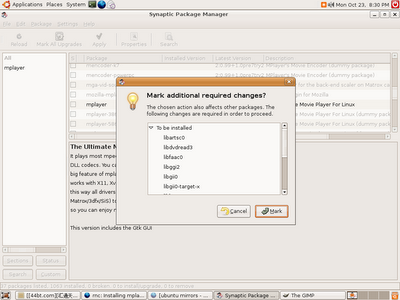
Step 7:
Once searched, click "Apply" on the same menu bar like Search. It will prompt you a list of to be installed programs.
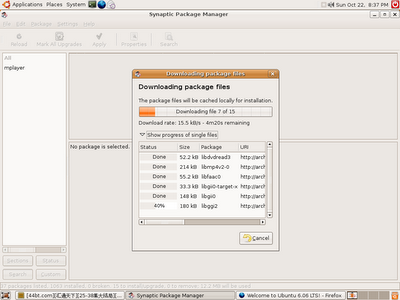
Step 8:
Your system might not have the CODECS requires to play RMVB files. repeat the steps again, but this time search for "win32codecs". Good luck.
The GUI Based of package management tool (Synaptic Packager Manager) alleviates the prerequisite of understanding and using apt-get, wajig and other similar kind of utilities.
Here, I presented a step by step guide on how to setup your UBUNTU box to enable it to play RMVB (A famous media file format, usually used to share video on BitTorrent network in Asia).
Step 1:
From the taskbar, access Application then Add/Remove Applications.

Once activated, the program need to conduct some checks on installed components and their dependencies and etc. You just gotta wait.

Step 2:
Click on the Advanced button on your bottom left corner of the Add/Remove Applications window.

Step 3:
Then you will be in Advanced mode.
Note: The system might prompt you to enter password for authorization.
Step 4:
You need to add a new entry to the repository. Activate the repository settings screen through Settings -> Repositories from the same window.

Step 5:
Add a new channel, by click on Add button.

Make sure you select all the options on the Add Channel screen. and click Add.

Step 6:
Once added, you click on the Reload button on your top left corner to refresh the list of programs. Then You can start to search for this software called "mplayer".
Click on the Search button on the menu bar, and enter "mplayer" and hit search.
The search results should be displayed on the pane at your right handside.

Step 7:
Once searched, click "Apply" on the same menu bar like Search. It will prompt you a list of to be installed programs.

Step 8:
Your system might not have the CODECS requires to play RMVB files. repeat the steps again, but this time search for "win32codecs". Good luck.
Saturday, October 21, 2006
How do you pronounce IT in geek?
Adapted from WhatIs.com
1. While data has at least two alternate meanings, in computer science it's information that has been translated into a form that is more convenient to move or process. How do you pronounce data correctly?
a. "DAH-tuh"
b. "DAY-tuh"
Answer : b
2. If you work with databases, you're sure to come across SQL. But how do you pronounce it?
a. like "sequel" as "SEE-Kwill"
b. "ess cue-ell"
c. A & B
Answer : c
3. Schema derives from a Greek word for "form" or "figure." If you work with relational or object-oriented databases or programming languages, you may be familar with schema as the organization or structure for a database. How do you pronounce it?
a. "SHE-mah"
b. "SKEE-mah"
Answer : b
4. Debian is a popular and freely-available computer operating system that uses the Linux kernel and other program components obtained from the GNU project. How do you pronounce it?
a. "deb-ee-an"
b. "dub-eye-an"
Answer : a
5. The word "cache" comes from the French, though the meaning is quite the same in either language: to store something where it can be easily retrieved for future use. It's also a noun, referring to that store itself. How is "cache" pronounced in common English usage?
a. "catch"
b. "cash"
Answer : b
6. VoIP use has proceeded rapidly over the past few years. Services like Skype and Vonage have attracted millions of users. Cisco products are increasingly being implemented in call centers. How should you be pronouncing it?
a. "voyp"
b. as its acronym, like "vee - oh - eye - pee"
c. A & B
Answer: c
7. If you've used a wide area network (WAN), you've probably encountered the sysop, often a tech-savvy employee who receives a small stipend for trouble-shooting computer-related problems. How do you pronounce sysop?
a. "SIZZ-ope"
b. "SISS-op"
Answer : b
8. Linux was named by Linus Torvalds, who developed the kernel for the operating system at the University of Helsinki in Finland. Linux is everywhere now; adopted by government of Brazil and showing up in "skinny" versions in smartphones and other devices, notably the "$100 laptop." So how do you pronounce the name of the OS correctly?
a. "LIHN-nix"
b. "LIE-nooks"
c. "LEE-nooks"
Answer : a
9. Acronyms are everywhere in information technology - or should we say "IT?" An acronym is an abbreviation of several words in such a way that the abbreviation itself forms a word. Techies love them. BASIC, SIP, HTML, ASP, VoIP, ISP, SaaS, SOA, LILO; the list is goes on and on. We try to help you make sense of them in our daily IT Alphabet Soup trivia questions, but have you stopped to learn how to pronounce acronym itself?
a. "ah-KROH-nihm"
b. "AK-ruh-nihm"
Answer : b
10. In information technology, canonicalization (sometimes spelled canonicalisation) is the process of making something canonical -- that is, in conformance with some specification. To canonicalize (as well as the slightly less tortured variant to canonify) is to ensure that data conforms to canonical rules, and is in an approved format. Canonicalization is also a bit of a tongue twister - how do you pronounce it?
a. "ka-NOH-nihk-uhl-LIE-ZAY-shun"
b. "KA-nahn-nihk-uhl-ih-ZAY-shun"
Answer : b
Tuesday, October 17, 2006
IBM DB2 Exam 000-700
I did it in the reverse way. I took the exam 000-705, yet I still haven't take 000-700. It's time now to bridge the gap and to obtain the official title of BI Designer.
Following are the steps I took for the preparation:
My result sheet
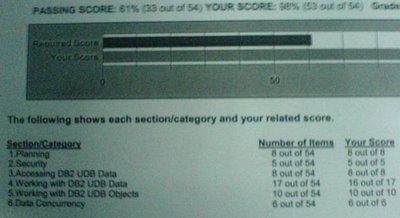
Some of the questions are pretty tricky. I shall not put the real questions here, but just to give you some clues, here is a similar one:
(Not REAL questions)
1.) If you gotta build DB2 application on XXX OS and it need to access YYYY OS DB2 Server when deployed, which of the following DB2 product is the minimal you need?
a. DB2 UDB Personal Edition
b. DB2 UDB Personal Edition with DB2 Connect Enterprise Edition
c. DB2 Personal Developer Edition
d. DB2 Universal Developer Edition
Answer is C. Because you need to build DB2 application, you need the SDK toolkit and at least a DB2 UDB PE for testing, therefore C is the minimal. D can be the answer is the question is not on MINIMAL because DB2 UDE includes every DB2 PDE components. A and B is definitely not the answer since it doesn't include SDK in the package.
and another typical kind of question.
2.) What should you catalog for a client to access a DB2 host database?
Answer: You need to catalog the remote server in the NODE directory, the remote database in the System DB directory AND remote database in the DCS directory since you need to use DB2 Connect to access host database. You need to understand the parameter use in these CATALOG statements.
Good luck for you folks that taking this exam.
Following are the steps I took for the preparation:
1. Read DB2 Family Fundamental Guide from IBM
6 chapters guide. Clear and concise to help you pass above 75%.
2. Read eLearning Crammer Course Material from colleague
Consists some sample questions and added notes for task 1. If you read this, 80% and above shouldn't difficult.
6 chapters guide. Clear and concise to help you pass above 75%.
3. Read a 400 pages book
DB2® Universal Database™ V8.1 Certification Exam 700 Study Guide
By Roger E. Sanders
Must read if you plan to get 85% and above.
4. Use DB2 whenever possible
SQL section constitutes 31% of exam. Practice makes perfect. I wouldn't need to do this step since I'm already quite good in it. :p
Must do if 90% and above is your target
Note: No. No advanced SQL covered in the exam. No recursive SQL you bet!
My result sheet

Some of the questions are pretty tricky. I shall not put the real questions here, but just to give you some clues, here is a similar one:
(Not REAL questions)
1.) If you gotta build DB2 application on XXX OS and it need to access YYYY OS DB2 Server when deployed, which of the following DB2 product is the minimal you need?
a. DB2 UDB Personal Edition
b. DB2 UDB Personal Edition with DB2 Connect Enterprise Edition
c. DB2 Personal Developer Edition
d. DB2 Universal Developer Edition
Answer is C. Because you need to build DB2 application, you need the SDK toolkit and at least a DB2 UDB PE for testing, therefore C is the minimal. D can be the answer is the question is not on MINIMAL because DB2 UDE includes every DB2 PDE components. A and B is definitely not the answer since it doesn't include SDK in the package.
and another typical kind of question.
2.) What should you catalog for a client to access a DB2 host database?
Answer: You need to catalog the remote server in the NODE directory, the remote database in the System DB directory AND remote database in the DCS directory since you need to use DB2 Connect to access host database. You need to understand the parameter use in these CATALOG statements.
Good luck for you folks that taking this exam.
IBM DB2 Exam 000-705
To earn the title as IBM Certified Business Intelligence Designer, I got to get myself pass in two exams. 000-700 and 000-705. I already passed the 000-705 BI exam during IBM Malaysia sponsored workshop (It's free for IBM business partner).
Here is the summary of the 000-705 exam preparation and experience.
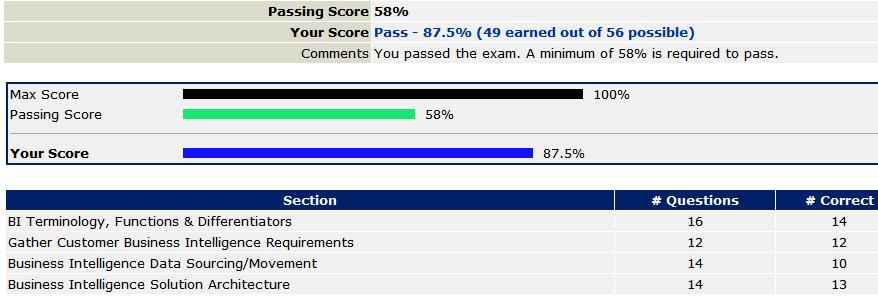
Scored a 87.5% or answered 49 questions correct out of total 56 questions.
Hit major bumper in the section "Business Intelligence Data Sourcing/Movement", which mostly the questions on replication and types of data warehouse processing (full, incremental, snapshot, etc).
705 is not a technical paper. If you have decent experience in data warehousing and business intelligence, then questions in the terminology, requirements and architecture are piece of cake.
Again, it is easy to pass, but hard to score and excel.
Here is the summary of the 000-705 exam preparation and experience.
1. 3 days of IBM DWE V9 bootcamp
Hmmm, not that relevant to the 705 exam, more like IBM try to equip its' business partners presales skills on the new DB2 DWE. It covers topics like the new Design Studio, Intelligent Miner, Cube making and etc.
2. 1 day of 705 exam workshop
It is like a last minute top-up of the knowledge pertaining to the 705 exam objectives. The instructor covers the test objectives one by one, and goes through some sample questions.
3. Self study
Got myself the copy of study guide from IBM web site for BI Designer exam version 7, most of the concepts and theories are still applicable.
Found a few excerpts from the book
"Business Intelligence for the Enterprise",
ISBN: 0-13-141303-1
This book is only 240 pages and it tells you general "stories" of Business Intelligence. Personally, I found it not that useful for the exam, but still something interesting to read about.

Scored a 87.5% or answered 49 questions correct out of total 56 questions.
Hit major bumper in the section "Business Intelligence Data Sourcing/Movement", which mostly the questions on replication and types of data warehouse processing (full, incremental, snapshot, etc).
705 is not a technical paper. If you have decent experience in data warehousing and business intelligence, then questions in the terminology, requirements and architecture are piece of cake.
Again, it is easy to pass, but hard to score and excel.
Saturday, October 14, 2006
DB2 How to Empty a Table
In data warehouse environment, usually there is a need to clear out the contents of staging tables to prepare for a fresh set of extracted source data. You might also want to housekeep some historical aggregation according to some predefined schedules, which involves copying data from a table to another and subsequently removed all data from the copied table. These are just some of the examples that boiled down to the need of efficiently "truncate" a table.
Microsoft SQL Server and Oracle DBA are definitely enjoying the luxury of built-in table truncation functionality, through command like "TRUNCATE TABLE YourTableName".
Ok fine, but does IBM DB2 UDB, the so-called most scalable and performing RDBMS provide such option?
Before that, let me evaluate some of the options of removing rows from a table.
Option A:
DELETE FROM YourTable
Well, you can delete all rows using this statement. However when involving lot of records, transaction logging causes significant performanc degradation. Still, this option is acceptable if your application requires recovery of deleted rows.
Option B:
(Assume this is within the same transaction)
ALTER TABLE YourTable ACTIVATE NOT LOGGED INITIALLY;
DELETE FROM YourTable;
You managed to escape the bad luck of doing a lot of transaction logging. But wait a minute, constraint checking are still in force (Check yourself by doing explaining a DELETE FROM statement).
Option C:
(Assume this is within the same transaction)
SET INTEGRITY FOR YourTable OFF;
ALTER TABLE YourTable ACTIVATE NOT LOGGED INITIALLY;
DELETE FROM YourTable;
Again, you managed to skip the logging and check constraint and referential constraint checking, datalink integrity checking, and generation of values for generated columns. Primary/Unique Key constraints still enforced.
Option D:
LOAD FROM /dev/null of del REPLACE INTO YourTable
This is by far the most common workaround that I have seen for table truncation. It basically uses the LOAD utility on /dev/null for simulating the loading (replace) of no-data into the designated table. The same concept works for Windows environment.
You can also use similar IMPORT FROM /dev/null of DEL REPLACE INTO YourTable. There are some differences between IMPORT/LOAD.
Option E:
With a little bit of guts, you can drop and recreate the tables. This can be tedious if you got to recreate every constraints/views/etc that dependent on the "new" table.
Option F:
ALTER TABLE YourTable ACTIVATE NOT LOGGED INITIALLY WITH EMPTY TABLE
This is by far my favorite way of doing "TRUNCATE Table" in DB2.
Which ring suits you? You decide.
Microsoft SQL Server and Oracle DBA are definitely enjoying the luxury of built-in table truncation functionality, through command like "TRUNCATE TABLE YourTableName".
Ok fine, but does IBM DB2 UDB, the so-called most scalable and performing RDBMS provide such option?
Before that, let me evaluate some of the options of removing rows from a table.
Option A:
DELETE FROM YourTable
Well, you can delete all rows using this statement. However when involving lot of records, transaction logging causes significant performanc degradation. Still, this option is acceptable if your application requires recovery of deleted rows.
Option B:
(Assume this is within the same transaction)
ALTER TABLE YourTable ACTIVATE NOT LOGGED INITIALLY;
DELETE FROM YourTable;
You managed to escape the bad luck of doing a lot of transaction logging. But wait a minute, constraint checking are still in force (Check yourself by doing explaining a DELETE FROM statement).
Option C:
(Assume this is within the same transaction)
SET INTEGRITY FOR YourTable OFF;
ALTER TABLE YourTable ACTIVATE NOT LOGGED INITIALLY;
DELETE FROM YourTable;
Again, you managed to skip the logging and check constraint and referential constraint checking, datalink integrity checking, and generation of values for generated columns. Primary/Unique Key constraints still enforced.
Option D:
LOAD FROM /dev/null of del REPLACE INTO YourTable
This is by far the most common workaround that I have seen for table truncation. It basically uses the LOAD utility on /dev/null for simulating the loading (replace) of no-data into the designated table. The same concept works for Windows environment.
You can also use similar IMPORT FROM /dev/null of DEL REPLACE INTO YourTable. There are some differences between IMPORT/LOAD.
Option E:
With a little bit of guts, you can drop and recreate the tables. This can be tedious if you got to recreate every constraints/views/etc that dependent on the "new" table.
Option F:
ALTER TABLE YourTable ACTIVATE NOT LOGGED INITIALLY WITH EMPTY TABLE
This is by far my favorite way of doing "TRUNCATE Table" in DB2.
Which ring suits you? You decide.
Labels:
Data warehousing,
DB2,
Optimization,
Programming Tips,
SQL
Wednesday, September 13, 2006
Nearly Get Killed
A typical situation in Malaysia's major highway is that you are able to see so many trucks on the move, carrying containers, goods, woods, and any kind of transportable items you can imagine.
Another typical situation is the presence of unwanted objects on the road, obstacles I would call them that might hinder the smoothness of your driving experience. These are usually paper boxes, stones, relatively small objects.
Today, I learnt another lesson of why you shouldn't drive behind a large truck. Besides the risk of stones dropping on your windscreen from these vehicles, they also prohibit you from seeing what's up in front on the road.
Driving at the speed of 90-100 kilometers per hour, behind a truck (as you might guessed), I caught by surprise by a metal rod rolling towards my car, which I only saw after that bloody truck driver avoid it at last minute. Roughly 1.5 meter long, 30 cm diameter with some funny sting on it. On the left lane is another truck, while on the right lane is a Toyota Altis moved at the speed of 110kmph. I got no choice but to roll over that "thing". The car movement direction skewed nearly 70 degrees. What a stunt you might think, my life is indeed on the stake.
No life casualty due the impact, however my passenger's left wheel is rendered useless and the alloy rim slightly bended.
The morale of the story is that do not drives near any trucks in whatsoever direction; they are killing machine, although they failed to kill today. And beware of funny looking metal rod.
Another typical situation is the presence of unwanted objects on the road, obstacles I would call them that might hinder the smoothness of your driving experience. These are usually paper boxes, stones, relatively small objects.
Today, I learnt another lesson of why you shouldn't drive behind a large truck. Besides the risk of stones dropping on your windscreen from these vehicles, they also prohibit you from seeing what's up in front on the road.
Driving at the speed of 90-100 kilometers per hour, behind a truck (as you might guessed), I caught by surprise by a metal rod rolling towards my car, which I only saw after that bloody truck driver avoid it at last minute. Roughly 1.5 meter long, 30 cm diameter with some funny sting on it. On the left lane is another truck, while on the right lane is a Toyota Altis moved at the speed of 110kmph. I got no choice but to roll over that "thing". The car movement direction skewed nearly 70 degrees. What a stunt you might think, my life is indeed on the stake.
No life casualty due the impact, however my passenger's left wheel is rendered useless and the alloy rim slightly bended.
The morale of the story is that do not drives near any trucks in whatsoever direction; they are killing machine, although they failed to kill today. And beware of funny looking metal rod.
Sunday, September 10, 2006
Mistake Mistake
The multithreaded Java application I wrote in April 06 for extracting data from 90k files to IBM DB2 v8.2 system suffering from performance bottleneck when dealing with too many worker threads. This is a common issue for multithreading programming and that's why we got something called Thread Pool. While waiting for the extraction to be finished (God, it has been running for 30 hours and still executing at this moment), I took some initiatives to perform a code review, trying to identify possible programming faults. And oh yeah, found a potential program problem. See figures below
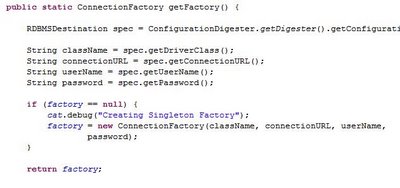
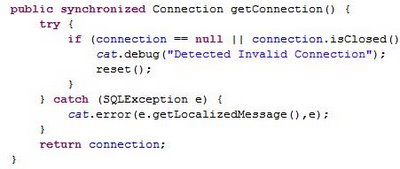
What you think is wrong with the above code snippets? Well, I try to recall the rationale of doing the stuff like that when I was developing this program and I think I did that to avoid the intricacy of thread synchronization due to very constrained assigned time frame.
I wouldn't tell you what's wrong with it and I hope you can spend some time exploring it out. However I can tell you that one of the way to get out from this scalability issue is to using java.lang.ThreadLocal to manage the connection instead.


What you think is wrong with the above code snippets? Well, I try to recall the rationale of doing the stuff like that when I was developing this program and I think I did that to avoid the intricacy of thread synchronization due to very constrained assigned time frame.
I wouldn't tell you what's wrong with it and I hope you can spend some time exploring it out. However I can tell you that one of the way to get out from this scalability issue is to using java.lang.ThreadLocal to manage the connection instead.
Tons of POS Transaction File
For the purpose of POC for a retail company's data mining initiative (again), I being trashed with 90k number of small files containing 1 year POS transactional data, nearly double the amount of files/data for previous POC effort. Almost 70% of these files are compressed in Z format. Made a quick study on java.util.zip package provided in Java SDK 1.4.2 (The package is available from SDK 1.1), no luck, the standard facility only supports ZIP and GZIP formats. Ok, fine. I made a search in sourceforge, looking for any open source java implementation. None of the search results are directly useful to my decompression need. Then, I tried Winzip, WinRAR, PowerZip and etc. Emmmm, most of the Windows GUI version of these programs are able to decompress Z archive, however none of them provide batch processing. Darn, I not going to decompress 90k files one by one, am I look like that dumb? Ok, thinking of command line version of Winzip and Winrar. Ooops, unfortunately enough, they don't supports Z format in their command line version.
Decided to do some research on Z archive and found this useful article
Uncompress gz and Z format
It seems to me that Z format and many other compression formats are natively supported by UNIX systems. So sad for Windows users.
Also, read this
Wikipedia: List of archive formats
Uppercase .Z is a different format compared to lowercase .z file. Generally .Z is produced using UNIX's compress command, whereby .z is by UNIX's pack command. Algorithms used for the compression are different too.
Since I only got limited time for this decompression task, I finally settled with GUNZIP program, that's freely available (http://www.gzip.org/) and performed a batch decompression. Proceed to the ETL phase then.
And here is a forum post that I found stating similar decompression requirement. Most probably I will use Runtime.exec to call out external utility such as GUNZIP, rather than trying to find a Java implementation for integration. Anyway, it's depends on the amount of time I have.
Similar Issue
Decided to do some research on Z archive and found this useful article
Uncompress gz and Z format
It seems to me that Z format and many other compression formats are natively supported by UNIX systems. So sad for Windows users.
Also, read this
Wikipedia: List of archive formats
Uppercase .Z is a different format compared to lowercase .z file. Generally .Z is produced using UNIX's compress command, whereby .z is by UNIX's pack command. Algorithms used for the compression are different too.
Since I only got limited time for this decompression task, I finally settled with GUNZIP program, that's freely available (http://www.gzip.org/) and performed a batch decompression. Proceed to the ETL phase then.
And here is a forum post that I found stating similar decompression requirement. Most probably I will use Runtime.exec to call out external utility such as GUNZIP, rather than trying to find a Java implementation for integration. Anyway, it's depends on the amount of time I have.
Similar Issue
Labels:
Compression,
Data warehousing,
Java,
Process,
SQL,
Tips and Tricks,
Work
Friday, September 08, 2006
Stay Alive 2006

Cool movie. I really like the idea of reading prayers before starting a game. That would be a nice start for any horror genre game. The movie begins with few gamers died in the same way as they did in the game they played, named Stay Alive. The scene where the guy with a pighead mask on the bed really amused me. Hahaha, I wonder what kind of simulation they're playing. Story continues with a group of friends then play the same game and one die after another. The only way to get out from the curse is to find a way to kill Elizabeth Bathory, the devilish character in the movie.
Check Elizabeth out
I don't give credit to the ending. As a matter of fact, the ending can definitely better than such typical kind.
And of course if such a game has been developed, I definitely will sign up as beta tester. Count me in.
CA Clarity Boot Camp '06 in Malaysia
After 3 weeks of intense boot camp training, finally the D day. Completed all exams with consistent scoring and time of completion, wonderful. *thumbs up*
A photoshooting session in the last day, and here is the Yahoo! photo album that contain pictures from one of my classmate's camera (Sony Cybershot W5).
Yahoo! photo album
And a souvenir from CA Malaysia as a token of appreciation for the completion of the course and certification. See below.

Name Card Holder
What most matter now is the prepareness into real world projects. Certification is one thing, implementation would be a totally different dimension. Good luck to every certified technical guys in my class.
A photoshooting session in the last day, and here is the Yahoo! photo album that contain pictures from one of my classmate's camera (Sony Cybershot W5).
Yahoo! photo album
And a souvenir from CA Malaysia as a token of appreciation for the completion of the course and certification. See below.

What most matter now is the prepareness into real world projects. Certification is one thing, implementation would be a totally different dimension. Good luck to every certified technical guys in my class.
Friday, September 01, 2006
Thursday, August 31, 2006
Installation of Clarity at home
As one of the preparation steps for CA Clarity Technical Certification, I did a fresh installation of Clarity 7.5.2 in my laptop.
I've used Microsoft SQL Server 2000 Developer Edition as the application database because of the operating system requirement for Enterprise edition. However, please note that this edition of SQL Server is not certified under the Clarity PAS for 7.5.2.
When I try to install the database from NSA, it seems that JDBC was unable to connect to the SQL Server. Then, I wrote a simple Java program to attempt to connect to the SQL Server using the shipped JDBC Driver (msbase.jar, msutil.jar, mssqlserver.jar), still the result remained.
Without wasting more time, I downloaded Service Pack 4 for SQL Server and installed it. This time, the connection was successful.
During the application database installation, the process terminated prematurely due to some collation errors. Geez, the server collation is Latin1_General_CP1_CI_AS and the database is SQL_Latin1_General_CP1_CI_AS and I suspect the installation script face difficulties in converting between these collations.
The installation guide specified SQL_Latin1_General_CP1_CI_AS as accepted collation for the database. SQL Server Enterprise Edition don't have this issue as I did numerous installations using Enterprise Edition without any bumper. Anyway, I dropped the database and created a new one with server collation instead.
No major issues faced after that.
And remember to fill in that installation report for submission to the support. :p
I've used Microsoft SQL Server 2000 Developer Edition as the application database because of the operating system requirement for Enterprise edition. However, please note that this edition of SQL Server is not certified under the Clarity PAS for 7.5.2.
When I try to install the database from NSA, it seems that JDBC was unable to connect to the SQL Server. Then, I wrote a simple Java program to attempt to connect to the SQL Server using the shipped JDBC Driver (msbase.jar, msutil.jar, mssqlserver.jar), still the result remained.
Without wasting more time, I downloaded Service Pack 4 for SQL Server and installed it. This time, the connection was successful.
During the application database installation, the process terminated prematurely due to some collation errors. Geez, the server collation is Latin1_General_CP1_CI_AS and the database is SQL_Latin1_General_CP1_CI_AS and I suspect the installation script face difficulties in converting between these collations.
The installation guide specified SQL_Latin1_General_CP1_CI_AS as accepted collation for the database. SQL Server Enterprise Edition don't have this issue as I did numerous installations using Enterprise Edition without any bumper. Anyway, I dropped the database and created a new one with server collation instead.
No major issues faced after that.
And remember to fill in that installation report for submission to the support. :p
Wednesday, August 30, 2006
Kingston Data Traveler II - Round 2
As far as I recalled, I tried to copy some hundreds of varying size files into the new Kingston Data Traveler II flash drive which I bought last week. Well, somehow the drive got strewed and it is permanently write protected. I can't create, rename or delete anything, besides reading out those files previously copied into the drive. After exhaustive googling and experiment with some low level disk formatting tools like killdisk, I gave up and sent an email to Kingston technical support regards this issue. They replied within 24 hours and recommended that I get a new replacement from one of their authorized distributor in Malaysia. Ok, the suggestion sounds logical and reasonable, but I prefer to get back to the shop where I bought it. That's it, finally I got a new drive from them and hopefully nothing will go wrong with this new born.
Sunday, August 27, 2006
Yummy! Yummy!

Got this cake from one of the local bakery store. Obviously enough, it is cappucino flavoured with strawberry garnish. Too sweet though. I still prefer cheese or tiramisu cakes. :)
New Storage Capacity
I managed to increase portion of existing personal IT storage through acquisition of the following items:
1.) SanDisk Memory Stick PRO Duo - 1GB

- Previously using SanDisk 64MB, which comes with the cell phone package.
- Price at RM175.00
- 5 years warranty
- Comes with adaptor
2.) Kingston Data Traveler II - 1GB

- Previously using Kingston 128MB
- Price at RM75.00
- 5 years warranty
Other future upcoming storage upgrades might includes:
1.) SanDisk Memory Stick PRO Duo - 1GB

- Previously using SanDisk 64MB, which comes with the cell phone package.
- Price at RM175.00
- 5 years warranty
- Comes with adaptor
2.) Kingston Data Traveler II - 1GB

- Previously using Kingston 128MB
- Price at RM75.00
- 5 years warranty
Other future upcoming storage upgrades might includes:
- Two 300GB Desktop HDD
Saturday, August 26, 2006
Thunder Storm in Kuala Lumpur
3 hours of non-stop raining in Kuala Lumpur, not that surprising caused traffic congestions of nearly every single routes and railways within the parameter of the city. In the past, this kind of natural disaster wouldn't be matter to me as I used to work or travel between outskirt of the city. Just how lucky I am, yesterday stuck at one of the little tiny bus station in front of KLCC, with my foot soaked with the water flooded out from no where. Waited for 5 minutes, then 15, the rain just seemed to get heavier and the lightning stroked endlessly. Ok, time's up, got to march to the KLCC LRT station before rush hour. Rolled up my pants and ran towards the building. Hit by the rain hard and almost blew by the strong wind to the sky. Oh yes, I’m totally wet, from top to bottom. Given no alternative, I had to purchase a shirt immediately from Isetan.
Story continues. The LRT station was way too crowded. I managed to cut through the queue (Which is not that ethical anyway), and tried to squeeze into the first train that came, not successful though. The experience is like you hitting a concrete wall or tries to squeeze into a matter where no space exists between atoms. Embarrassing though :p
Finally, got up on the next train. Picked up my car and jammed in the highway for 1 hour; reached home around 8pm. Phew, what a journey.
Well, it's just another rainy day in Malaysia. You just need to get use to it.
Story continues. The LRT station was way too crowded. I managed to cut through the queue (Which is not that ethical anyway), and tried to squeeze into the first train that came, not successful though. The experience is like you hitting a concrete wall or tries to squeeze into a matter where no space exists between atoms. Embarrassing though :p
Finally, got up on the next train. Picked up my car and jammed in the highway for 1 hour; reached home around 8pm. Phew, what a journey.
Well, it's just another rainy day in Malaysia. You just need to get use to it.
Saturday, August 19, 2006
Procrastinating usual productivity and knowledge discovery.
Virtually everyone I know, at certain period of time, suffers from the effect of procrastination. I, a mortal who tagged with the "nerd" label can’t really escapable from this universal law of human behavior.
So, that's it. Put aside all my reference e-book, paper books, and journal papers and shut down my Microsoft Outlook forcefully. I'm going to focus on one particular objective: To be extremely unproductive..... for a short moment.
My counter-productive measures include the following:
Walked mindlessly within house parameter - 10 minutes
Sat on massage chair and relax - 15 minutes
Took a nap on sofa chair - 20 minutes
Ate dinner (Without newspaper and reading materials around) - 15 minutes
Tried to speak to my dogs and failed - 20 minutes
And other similar activities - 1 hour.
It's kinda difficult for me to prolong my planned procrastination period. Felt so eager to sit down to my precious workstation and start to type something. Envy those slackers that are able to survive without using their brain for long period. Bravo, slackers.
Back to work.
So, that's it. Put aside all my reference e-book, paper books, and journal papers and shut down my Microsoft Outlook forcefully. I'm going to focus on one particular objective: To be extremely unproductive..... for a short moment.
My counter-productive measures include the following:
Walked mindlessly within house parameter - 10 minutes
Sat on massage chair and relax - 15 minutes
Took a nap on sofa chair - 20 minutes
Ate dinner (Without newspaper and reading materials around) - 15 minutes
Tried to speak to my dogs and failed - 20 minutes
And other similar activities - 1 hour.
It's kinda difficult for me to prolong my planned procrastination period. Felt so eager to sit down to my precious workstation and start to type something. Envy those slackers that are able to survive without using their brain for long period. Bravo, slackers.
Back to work.
Saturday, July 29, 2006
K.L. Method
The most popular statistical method for dimensionality reduction of a large data set is the Karhunen-Loeve (K-L) method, also called Principal Component Analysis.
Principal component analysis is a method of transforming the initial data set represented by vector samples into a new set of vector samples with derived dimensions. The goal of this transformation is to concentrate the information about the differences between samples into a small number of dimensions.
More formally, the basic idea can be described as follows: A set of n-dimensional vector samples X = {x1, x2, x3 …, xm} should be transformed into another set Y = {y1, y2, …, ym} of the same dimensionality, but Y have the property that most of their information content is stored in the first few dimensions. This will allow us to reduce the data set to a smaller number of dimensions with low information loss.
Thursday, July 27, 2006
Discovered Friend's Blog
Found a few blog of my friends. Added to the navigation links to the right.
Wednesday, July 26, 2006
Business Trip in Kerteh - Part Five

Usual day breakfast in resort. Variety of food includes Terengganu's Special, Western, Chinese, Malay, Indian, Cereal, etc.

Almond Rocha Mocha, is just a mixture of mocha with topped cream. Cost me more than RM14.

Giant chess set for play.

This is the place where you can rent golf shoe, golf set, buy the token for golf balls and other sports equipments. Drives by the impulse to try Awana Kijal's driving range, I rent the following:
Half golf set -> RM 25.00
50 golf balls -> RM 5.00
I didn't rent the golf shoe and thus the personnel warned me of the possible risks of getting injured and the shop will not be liable on it. Blah.. blah..

Embrassment occured when I tried to get the golf balls out from the auto-dispenser, I forgot to put in the basket before activating the dispensement. Can you imagine 50 balls flushed out from the machine and scattered around the driving range? Hahahaha, please keep it as secret :p. I spent around 1 hour for swinging out 50 balls. Not a bad driving range, just that some part of it still under renovation.
Business Trip in Kerteh - Part Four

Mr. Ki and Mr. Jal welcome you.

Climb up there and have a nice view.

Obey the guidance please.

A bunche of guy playing beach volley ball. Boring.

Not an extraordinary beach of course, if compared to Redang or Lang Tengah.
Business Trip in Kerteh - Part Three

Walking on the back of the main building towards outdoor facilities and beach.

Overview of what you can expect.

Two tennis courts available. No time to utilize it, though.

Nice pool side cafeteria.

Not a bad swimming pool at all. No, it's not my intention to put that guy in the picture. Girls preferred.

Two jacuzzi pools available for usage.
Business Trip in Kerteh - Part Two

Awana Kijal's lobby, nothing special.


The theme of this resort is towards a more greenish and natural environment. You can see artificial plants around the place.

Night view of lobby.
Business Trip to Kerteh - Part One

Sadly, no plasma tv in the room. Well, 29inch CRT tv would do since most of the time will not be in the hotel.

Weird and freaky placement of bath tube at the corner. Not really know how to enjoy that.

Going to sleep on this bed for the next two to three nights.... alone.

Didn't see any needs to use these small chairs.
Wednesday, July 12, 2006
Chicken or Egg
A good old riddle, which one comes first? Chicken or Egg? We can spend ages debating on this matter. Similarly, we can ask ourselves: Business or Technology, which one drives the other?
Looking at the history of mankind, we realized that technology exists since the time when we start doing business. From a perspective, we can even argue that it is technology that enables the performance of business activity. In modern day, the dependencies between business and technology are even more inter-twined than ever that the failure of either one causes a disastrous impact on the other. Bad Business Performance can cause reduction in IT budget and ridiculously insufficient IT budget can prevent the business from attaining competitive advantage and thus loss of business opportunities.
To paint a clearer picture of the synergy between business and technology, I would like to introduce "Demand" as a mediator for this relationship. It is Demand that drives both business and technology, whether it is market demand, regulatory demand or even religion demand. Either side of the relationship which responds to Demand will eventually stimulates the evolution of the other to achieve a harmonized balance.
Take one simple example from ITIL IT Service Management chapters, Business Continuity Management or Contingency Planning requires the incorporation of both a business element (Business Continuity Planning) and a technology element (IT Service Continuity Planning) because for any service-oriented organization to continue provide the agreed level of service the business and IT must be aligned. Unless your company is truly independent of any technology, else you must plan for the unexpected, both in terms of business and technology risks.
Looking at the history of mankind, we realized that technology exists since the time when we start doing business. From a perspective, we can even argue that it is technology that enables the performance of business activity. In modern day, the dependencies between business and technology are even more inter-twined than ever that the failure of either one causes a disastrous impact on the other. Bad Business Performance can cause reduction in IT budget and ridiculously insufficient IT budget can prevent the business from attaining competitive advantage and thus loss of business opportunities.
To paint a clearer picture of the synergy between business and technology, I would like to introduce "Demand" as a mediator for this relationship. It is Demand that drives both business and technology, whether it is market demand, regulatory demand or even religion demand. Either side of the relationship which responds to Demand will eventually stimulates the evolution of the other to achieve a harmonized balance.
Take one simple example from ITIL IT Service Management chapters, Business Continuity Management or Contingency Planning requires the incorporation of both a business element (Business Continuity Planning) and a technology element (IT Service Continuity Planning) because for any service-oriented organization to continue provide the agreed level of service the business and IT must be aligned. Unless your company is truly independent of any technology, else you must plan for the unexpected, both in terms of business and technology risks.
Thursday, July 06, 2006
Is Your Core Business IT System Crucial?
Imagine a large automobile sales, services and supports organization with tons of branches and dealers to manage. Lots of functional IT systems are running concurrently and yet they interacts with each other and to external parties. Suppliers, employees, customers and management are relying on these heterogeneous systems to carry out their daily routine.
In this situation, I need to ask again: Is your core business IT System crucial? Added up to that question, Can your enterprise systems evolve? The reasons for software evolution are varying but they all serve one ultimate purpose: to make sure the business continues to survive.
What you think will happen if one day they need to:
As many real world examples pointed out, many enterprise projects are unsuccessful due to one main reason: They can't evolve in a way that's effective, efficient and minimized risk.
Enterprise applications are totally different from many other sorts of software. As an enterprise architect, you gotta think in a macroscopic level and execute in microscopic details.
In past one month, I was involved in such a scenario where a team of programmers is assigned the mandate to evolve a business core system, mainly in the area of bug fixing and functionality enhancement.
Some of my findings are summarized as below:
To be continued. Stay Tune. :)
In this situation, I need to ask again: Is your core business IT System crucial? Added up to that question, Can your enterprise systems evolve? The reasons for software evolution are varying but they all serve one ultimate purpose: to make sure the business continues to survive.
What you think will happen if one day they need to:
1. Add a new functional module to existing system
2. Customize existing workflow
3. Deploy a feature enhancement
4. Patch a found bug
5. Interface with a new external authority party
6. Optimize runtime performance
.... And so many else.
As many real world examples pointed out, many enterprise projects are unsuccessful due to one main reason: They can't evolve in a way that's effective, efficient and minimized risk.
Enterprise applications are totally different from many other sorts of software. As an enterprise architect, you gotta think in a macroscopic level and execute in microscopic details.
In past one month, I was involved in such a scenario where a team of programmers is assigned the mandate to evolve a business core system, mainly in the area of bug fixing and functionality enhancement.
Some of my findings are summarized as below:
The Good:
1. Architectually, the system is well designed with plenty of design patterns applied and plenty of property files (It might not be good, heard about XML configuration hell?) available for attaching loosely coupled and late bound components.
2. Well known open source frameworks and components were used. Struts, Hibernate, Apache Commons, Log4J, WebDoclet, etc.
3. Presentation tier and business tier are relatively well encapsulated with defined access points.
4. The use of ThreadLocal for managing Hibernate session
5. The use of dynamic proxy to manage DAO method invocations (Though the implementation is less than satisfactory)
(Trying very hard to think out more.... But can't seems to find any other good point)
The Bad:
1. Running on IBM WebSphere 5.1, developers actually mixed the usage of Struts TagLib and JSTL. Personally, I wouldn't do that, as many of JSTL functionalities overlapped with Struts related taglibs and since JSTL is not part of the JSP 1.2 yet, my advice is to stick with Struts only. Putting in JSTL in this case will make the deployment difficult and future upgrade to newer version of J2EE container more troublesome.
2. Unnecessary coupling between the core framework classes with web application related classes. Imagine one of your core engine class actually reference your /WEB-INF/classes's class. Cyclic dependencies cause the original ant script to fail.
3. Existence of two separate mechanisms to obtain database connections. One is using hibernate session, another is direct JNDI lookup. Hey dude, can't you just use one? In the new version of the system, I refactored the codebase to use only the hibernate session because previous JNDI lookup mechanism involved plenty of property configuration files, each for different components (HUH?).
And more....
The Evil: (We got our winners here)
1. Drag and drop deployment mechanism
- I was fainted when first saw this deployment process. To deploy new classes to the production server, you "drag and drop" your classes directly through FTP interface to their respective directories. Imagine you got 10+ updated and new classes in different java package need to be deployed, how inefficient it is to find each of the respective directory, drop the file, cross your finger and hope the container load it properly and continue with the next.
2. Minimal or no documentations
- Well, no need to speak much about this. Even the business process is not properly documented and most of the time you will like "Huh, how come the button still disabled? Do I need to perform anything anywhere else?"
3. Not a single unit test
- Without unit test, how can you confidently perform your integration test? In fact, high latency was resulted from the minor configuration issue like miss out a mapping entry in hibernate configuration file, which is suppose to be discovered during unit testing.
4. Business requirements not properly logged.
- From time to time, developers and analysts asking themselves: Emmmm, this looks familiar, was it implemented before? Oops, I can't really tell, grant me 2 days to trace through the code again.
5. Problematic concurrent transactions
- Lost Updates did happen. E.g. Stock quantity discrepancies
6. Poor Exception Handling
- I don't even want to mention about this
To be continued. Stay Tune. :)
Sunday, June 25, 2006
The ten fallacies of enterprise computing
Continuing from the previous journey in Java Reflection In Action, I've chosen another route into enterprise computing. Effective Enterprise Java by Ted Neward, if you insisted want to know the book name. Below is an excerpt of the listing of the ten fallacies of enterprise computing from the book's chapter 1.
1. The network is reliable.
2. Latency is zero
3. Bandwidth is infinite
4. The network is secure
5. Topology doesn't change
6. There is one administrator
7. Transport cost is zero
8. The network is homogeneous
9. The system is monolithic
10. The system is finished
On these 10 rules is much of this book built.
Amazon.com: Effective Enterprise Java: Books: Ted Neward
1. The network is reliable.
2. Latency is zero
3. Bandwidth is infinite
4. The network is secure
5. Topology doesn't change
6. There is one administrator
7. Transport cost is zero
8. The network is homogeneous
9. The system is monolithic
10. The system is finished
On these 10 rules is much of this book built.
Amazon.com: Effective Enterprise Java: Books: Ted Neward
Saturday, June 24, 2006
Finished Java Reflection In Action. Level Up.
2 weeks ago, while i'm searching for resources about Java's Dynamic Proxy around the you-know-where, found Java Reflection In Action by Ira R. Forman, Nate Forman (They are father and son, how interesting) which chapter 4 putting java.lang.reflect.Proxy in action. Attracted by the materials i read from this book, I instantly get a copy of it and start reading from the beginning till the end like the time when i was reading Davinci Code :p.
No matter whether you are novice or experienced Java developer, I believe that this book helps you to consolidate knowledge that you gained from your works, especially when you're maintaining someone else codes and wonder the rationale why the original developers designed it like a monster you struggled to overcome. It also give you a solid overview of meta-level objects in Java 1.4 (Thos book was published in 2004) and ClassLoader that I personally found useful.
However, IMHO, the lengthy few chapters about C2C framework are too redundant, especially when the author described the application of C2C framework for applying design patterns. One or two such examples are inspiring, but too many of them makes me skipped them directly. Anyway, the understanding is more essential right?
Lastly, I must compliment this book for making me fully occupied my time in the past few days :)
Amazon.co.uk: Java Reflection in Action: Books
No matter whether you are novice or experienced Java developer, I believe that this book helps you to consolidate knowledge that you gained from your works, especially when you're maintaining someone else codes and wonder the rationale why the original developers designed it like a monster you struggled to overcome. It also give you a solid overview of meta-level objects in Java 1.4 (Thos book was published in 2004) and ClassLoader that I personally found useful.
However, IMHO, the lengthy few chapters about C2C framework are too redundant, especially when the author described the application of C2C framework for applying design patterns. One or two such examples are inspiring, but too many of them makes me skipped them directly. Anyway, the understanding is more essential right?
Lastly, I must compliment this book for making me fully occupied my time in the past few days :)
Amazon.co.uk: Java Reflection in Action: Books
Thursday, May 18, 2006
PKCS List Out
PKCS #1 : RSA Encryption Standard
PKCS #3 : Diffie-Hellman Key Agreement Standard
Note: PKCS #2 and #4 combined together in the PKCS #1
PKCS #5 : Password Based Encryption Standard
PKCS #6 : Extended Certificate Syntax Standard
PKCS #7 : Cryptographic Message Syntax Standard
PKCS #8 : Private Key Information Syntax Standard
PKCS #9 : Selected Attribute Types
PKCS #10 : Certificate Request Syntax Standard
PKCS #11 : Cryptographic Token Interface Standard
PKCS #12 : Personal Information Exchange Standard
PKCS #13 : Elliptic Curve Cryptography Standard
PKCS #14 : Pseudu-Random Number Generator Standard
PKCS #15 : Cryptographic Token Information Format Standard
PKCS #3 : Diffie-Hellman Key Agreement Standard
Note: PKCS #2 and #4 combined together in the PKCS #1
PKCS #5 : Password Based Encryption Standard
PKCS #6 : Extended Certificate Syntax Standard
PKCS #7 : Cryptographic Message Syntax Standard
PKCS #8 : Private Key Information Syntax Standard
PKCS #9 : Selected Attribute Types
PKCS #10 : Certificate Request Syntax Standard
PKCS #11 : Cryptographic Token Interface Standard
PKCS #12 : Personal Information Exchange Standard
PKCS #13 : Elliptic Curve Cryptography Standard
PKCS #14 : Pseudu-Random Number Generator Standard
PKCS #15 : Cryptographic Token Information Format Standard
Wednesday, May 17, 2006
Some PKI-related Regulations
I plan to read through the following United States regulations. Just wondering when I will have that kind of time?
CA — www.ss.ca.gov/digsig/regulations.htm
NC — www.secretary.state.nc.us/ecomm/ecrules.htm
TX — www.dir.state.tx.us/standards/srrpub13.htm
CA — www.ss.ca.gov/digsig/regulations.htm
NC — www.secretary.state.nc.us/ecomm/ecrules.htm
TX — www.dir.state.tx.us/standards/srrpub13.htm
Monday, May 15, 2006
Introducing CalvaryZone
My best pal in INTI Subang Jaya, doing great with his photography careers. :)
You can visit his FlickR through one of the link at the site bar.
And dude, why you never take your own pictures? :p
You can visit his FlickR through one of the link at the site bar.
And dude, why you never take your own pictures? :p
Monday, May 08, 2006
Bullish KLSE... Finally
2.1 Billion transaction volume. WOW. That should be a strong rallying signal most retail investors awaiting for quite some time.
Being through few years of consolidation, it seems like investors are kinda optimistic and motivated when the market sentiment turning green only for a few days.
Yes, i admitted that the KLSE index has passed the critical resistance line of 954 and showing strong uptrend, but always remember that index is controlled by the component stocks and thus might not be reflecting the actual distribution of increment margin among all the counters. Plenty of good quality stocks still at their previously plunged price (Yeah, great chance to put your hot money into these and wait for the good news).
For those that closely observed KLSE for the past few years, they know that Malaysia KLSE is kinda weird and pathetic. In the past, announcement of good news doesn't linearly correlated to the market movement. Political stability, increased GDP, RM unpegged and so many other positive news failed in the attempt in rejuvenating this market. The difference is that each of them comes one after another and usually is countered by another negative happening.
This time, retrenchment of crude oil price below USD70, greatly increased appreciation of RM against USD, more generous 9MP plan, stronger political determination (Voiced against ex-PM comments), cleaning up of lame public servants, better corporation outlook and more stable regional political status. Not to mention possible rate hike of TNB electricity and interest rate.
Too good to be true? You bet on it. The question now is: How long will the effect of goodness sustains before the next wave of negativity comes? One week or less? No one will know. The best part is that you can just grab as much money as you can, and runaway with it now.
Rebellous IRAN against US demands, possible greater trade deficit, returns of oil price nightmare, uncontrolled inflation rate, busts of local property market, political instability of Thailand and Indonesia (Again!) and fall back on regional competition. Hahahaha, yeah, now you know what is awaiting you at the end of this road. The best of these is, once the bubble of speculated, high volume counters busted, it is the domino effect that I personally would enjoy to see. Remember IRIS? or even better remember Tech Venture?
Being through few years of consolidation, it seems like investors are kinda optimistic and motivated when the market sentiment turning green only for a few days.
Yes, i admitted that the KLSE index has passed the critical resistance line of 954 and showing strong uptrend, but always remember that index is controlled by the component stocks and thus might not be reflecting the actual distribution of increment margin among all the counters. Plenty of good quality stocks still at their previously plunged price (Yeah, great chance to put your hot money into these and wait for the good news).
For those that closely observed KLSE for the past few years, they know that Malaysia KLSE is kinda weird and pathetic. In the past, announcement of good news doesn't linearly correlated to the market movement. Political stability, increased GDP, RM unpegged and so many other positive news failed in the attempt in rejuvenating this market. The difference is that each of them comes one after another and usually is countered by another negative happening.
This time, retrenchment of crude oil price below USD70, greatly increased appreciation of RM against USD, more generous 9MP plan, stronger political determination (Voiced against ex-PM comments), cleaning up of lame public servants, better corporation outlook and more stable regional political status. Not to mention possible rate hike of TNB electricity and interest rate.
Too good to be true? You bet on it. The question now is: How long will the effect of goodness sustains before the next wave of negativity comes? One week or less? No one will know. The best part is that you can just grab as much money as you can, and runaway with it now.
Rebellous IRAN against US demands, possible greater trade deficit, returns of oil price nightmare, uncontrolled inflation rate, busts of local property market, political instability of Thailand and Indonesia (Again!) and fall back on regional competition. Hahahaha, yeah, now you know what is awaiting you at the end of this road. The best of these is, once the bubble of speculated, high volume counters busted, it is the domino effect that I personally would enjoy to see. Remember IRIS? or even better remember Tech Venture?
Wednesday, May 03, 2006
Oblivion Tip: Skeleton Key
At the level 30, my lockpicking is still stucked at 22. Well, this is expected as my oblivion player specialization is in magic. However, there is a quest to find The Eye of Nocturnal and the reward for this quest is a special item called Skeleton Key that will increase your lockpicking skill by a whooping 40 (O yeah, +40). This key wouldn't break and thus you can throw away all your lockpickers without a pain.
Read More
You must be at least level 10 to do this.
To get to the shrine, go to the city of Leyawiin and take the eastern road to the north. Keep an eye out for a bunch of people standing around, also look for the sign that says "County Kvatch". Take the bridge to the shrine and talk with the shrine. She will give you a quest to find the Eye of Nocturnal. First thing you need to do after you get the quest is to spy on a couple of thieves in Leyawiin. They will give you all the information you need on finding the right cave. In the dungeon, you will have to fight or sneak past a bunch of trolls. These guys are pretty tough but, the reward is well worth your trouble.
Read More
Monday, May 01, 2006
This book might save your life.
A great initiative from Malaysian Bar Council. I might print a copy and put it in my car just in case of any described circumstances happened. However, the true effectiveness of the steps outlined in the booklet will only be convinced and proves to be practical when there is enough "real world application". I can imagine a scenario where some irresponsible police tear the booklet into million pieces in front of you and drag you back to police station without you got chances to exercise any of your rights. Ideal is one thing, the truth is another.. as usual.
Malaysian Bar: Police and Your Basic Rights
Malaysian Bar: Police and Your Basic Rights
Monday, April 17, 2006
Formal Context
A formal context is a triple of sets (O,A,I)
where
O is a set of objects
A is a set of attributes
I is a binary relation between A and O (O X A Matrix)
The notation oIa,
where
o is a member of O
a is a member of A
(o,a) is a member of I
More simply, the formal context can be visualized as a vector space model
where each row represents an object from O and each column represents an attribute from A. Each matrix element presents the occurence/existence of attribute a in object o. Various variant of such a model exists with the different being the matrix element function. For example, the matrix element value might represent the degree of significant of the attribute a in object o, instead of simply representing the existence.
where
O is a set of objects
A is a set of attributes
I is a binary relation between A and O (O X A Matrix)
The notation oIa,
where
o is a member of O
a is a member of A
(o,a) is a member of I
More simply, the formal context can be visualized as a vector space model
where each row represents an object from O and each column represents an attribute from A. Each matrix element presents the occurence/existence of attribute a in object o. Various variant of such a model exists with the different being the matrix element function. For example, the matrix element value might represent the degree of significant of the attribute a in object o, instead of simply representing the existence.
Sunday, April 16, 2006
Ahem Ahem. Listen to this...
漫長的路
仰望著天空 看到了滿天的秘密
快告訴我 我是喝醉了
愛吧 笑吧 相信吧 等吧
我在等 等著熟悉的今天
因為今天不在是屬於我一個人
進步是當你決定放手一搏的時候 放手一搏吧
我 只想換回一個真正的我
NERD MUST HAVE: Ergonomic Handkerchief

This series of handkerchief comes with a nose pouch, which supposed your nose will fits in when you sneezed. Theoretically this design should catch everything that your nose throws out. But practically the design will causes the creation of region on the handkerchief with high density cluster of germs. Such distribution can results in uneven utilization of handkerchief spaces and likely to be difficult to be washed.
To counter with the density issue, I proposed that the handkerchief fabric materials should be chosen that allows the absorption of mucus and distribution to areas of handkerchief based on current density level.
Just another bored posting. :p
Saturday, April 15, 2006
Flashbag Flash Drive
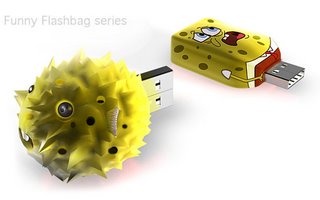



The idea of FlashBag is to provide sort of visual cue to indicate to the owner the utilized space of the Flashdrive. No a bad concept, as you might not need to plug in the drive to actually check out the remaining capacity. However, besides the creativity and entertaining effects of the Flashbag, I doubt it poses any real usefulness. Some of the disadvantages include blockage of the surrouding space near USB port, imprecise reflection of the remaining space when the Flashdrive capacity is too large, and you might even get yourself caught as suspicious terrorist members when going through the airport check.
Keep it simple, a digital gauge indicator is definitely better.
PlusMinus Design
Subscribe to:
Posts (Atom)

